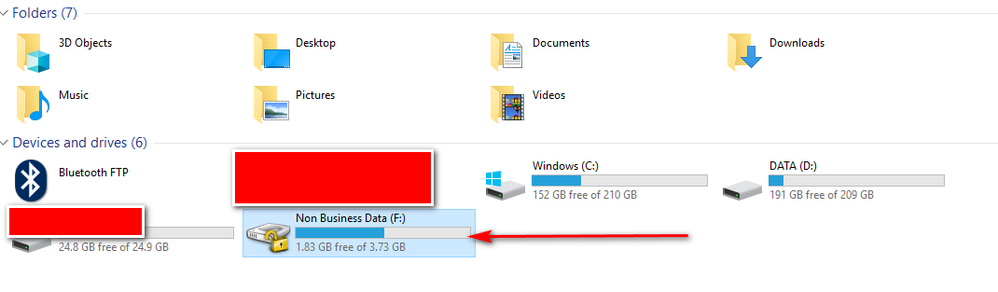
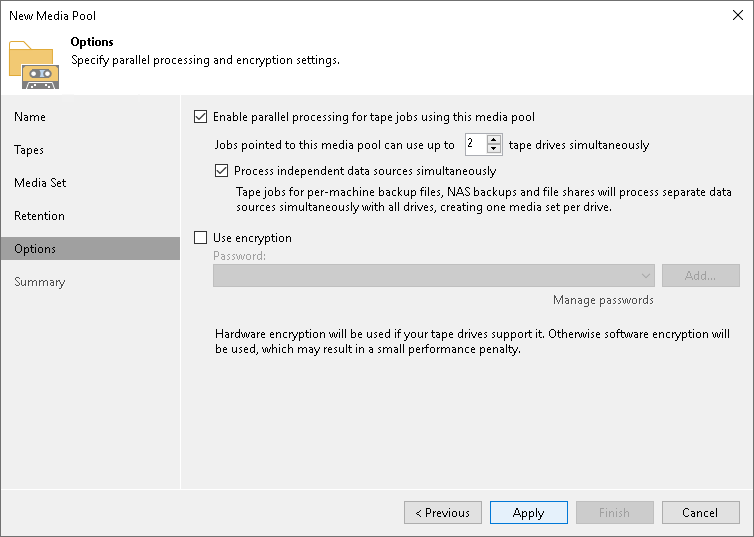
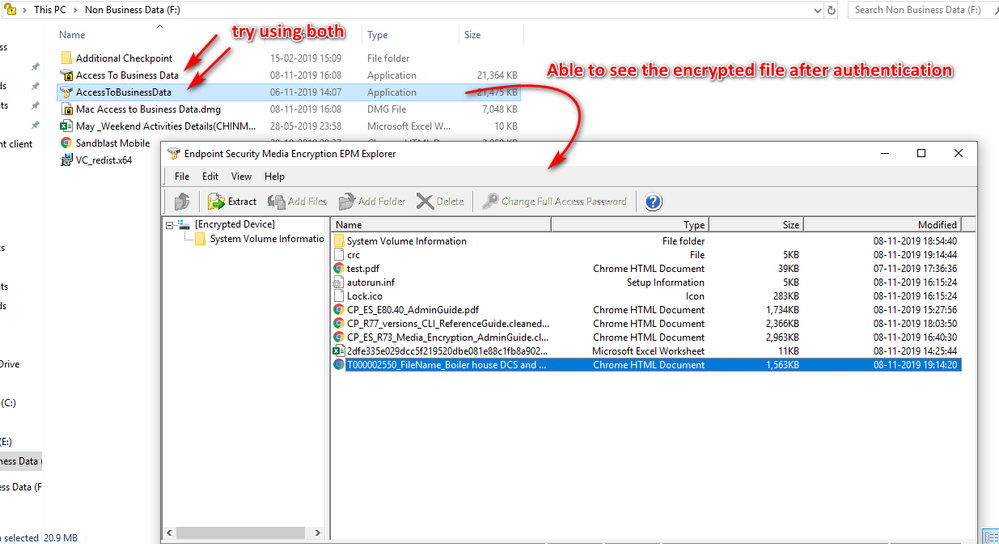
FEATURE REQUEST: Symantec Endpoint Encryption Removable Media Encryption event logs should be visible from the management server.

Entropy | Free Full-Text | A Chaotic-Based Encryption/Decryption Framework for Secure Multimedia Communications




![KB7406] ESET Endpoint Encryption Removable Media Encryption (RME) Policies KB7406] ESET Endpoint Encryption Removable Media Encryption (RME) Policies](https://support.eset.com/storage/IMAGES/en/%208347_KB7406/workstation_policy_rmemode.png)
![KB7166] Decrypt a memory stick or external disk using ESET Endpoint Encryption KB7166] Decrypt a memory stick or external disk using ESET Endpoint Encryption](https://support.eset.com/storage/ESET/Platform/Publishing/images/Authoring/ImageFiles/ESET/KB_ENG/deslock_KB7166_step2a.png)

![KB8028] Encrypt optical media in ESET Endpoint Encryption KB8028] Encrypt optical media in ESET Endpoint Encryption](https://support.eset.com/storage/IMAGES/en/9660_KB8028/KB8028Fig1-1a.png)