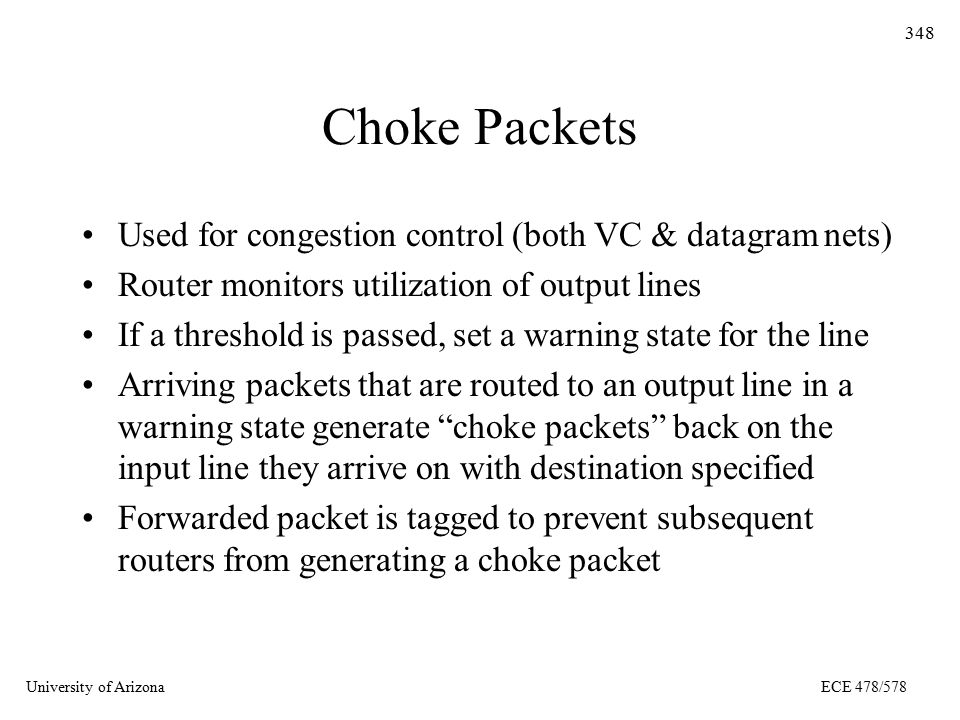
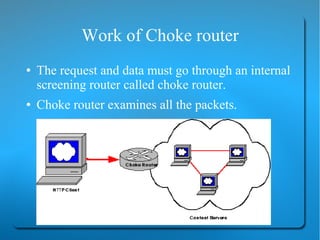
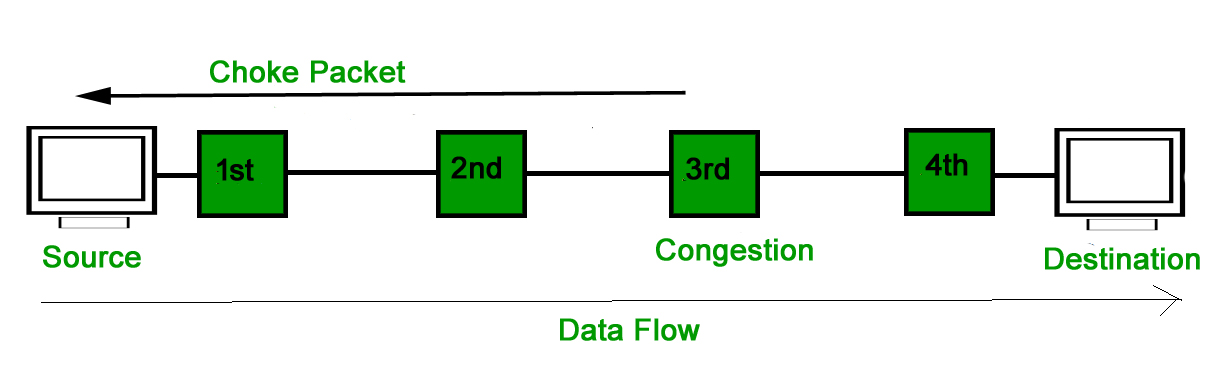
University of ArizonaECE 478/ Choke Packets Used for congestion control (both VC & datagram nets) Router monitors utilization of output lines If. - ppt download

Understanding Edge Routing and the WAN in the Virtualized IT Data Center - Technical Documentation - Support - Juniper Networks

Amazon.com: NETGEAR Nighthawk WiFi 6E Router (RAXE300) | AXE7800 Tri-Band Wireless Gigabit Speed (Up to 7.8Gbps) | New 6GHz Band | 8-Streams Cover up to 2,500 sq. ft, 40 Devices : Everything Else




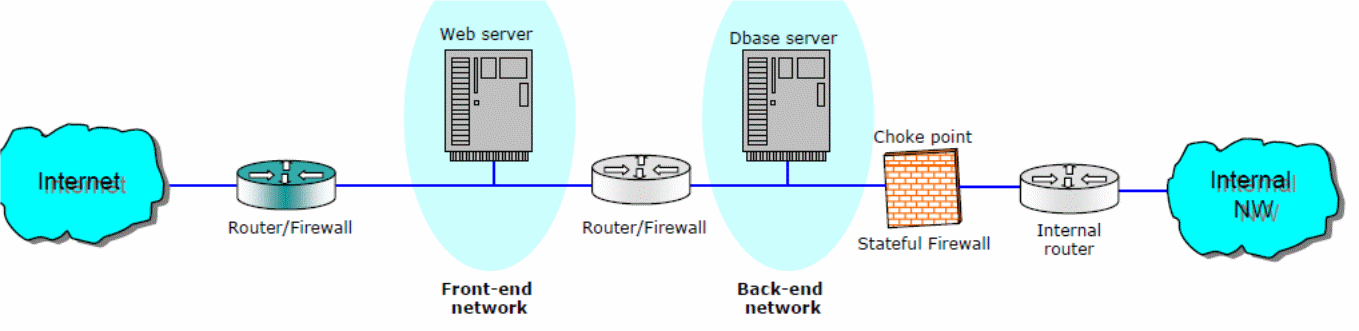
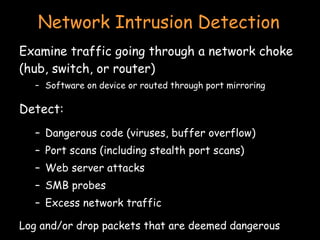

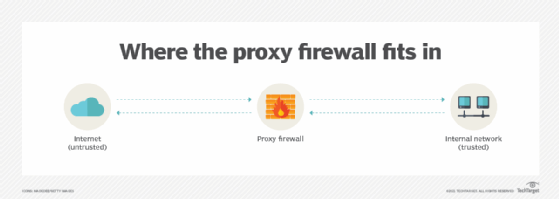






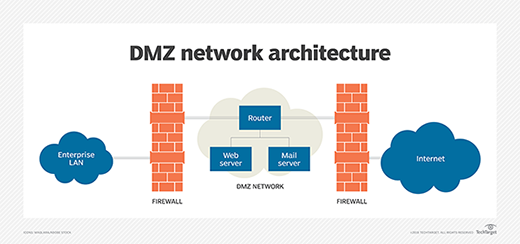
![Chapter 4] 4.2 Firewall Architectures Chapter 4] 4.2 Firewall Architectures](https://docstore.mik.ua/orelly/networking/firewall/figs/fire0404.gif)
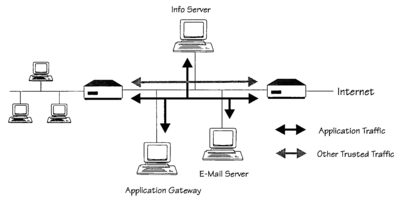

![Chapter 4] 4.2 Firewall Architectures Chapter 4] 4.2 Firewall Architectures](https://docstore.mik.ua/orelly/networking/firewall/figs/fire0403.gif)