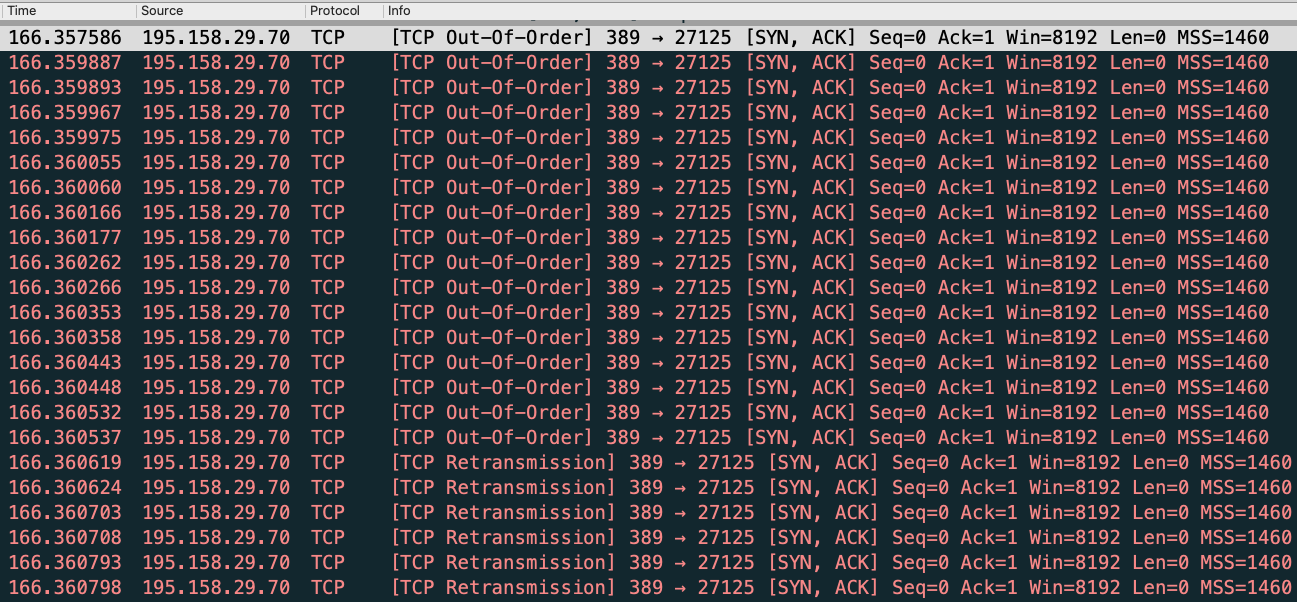
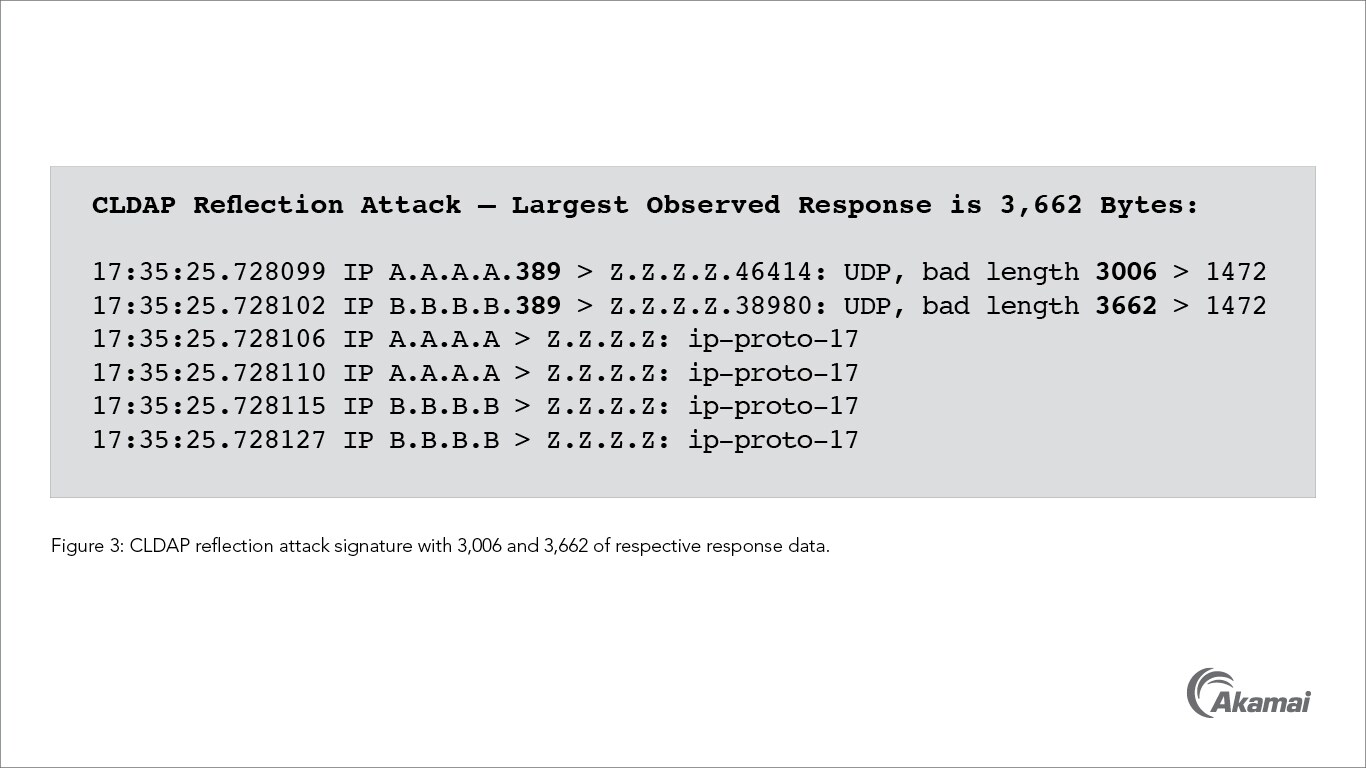
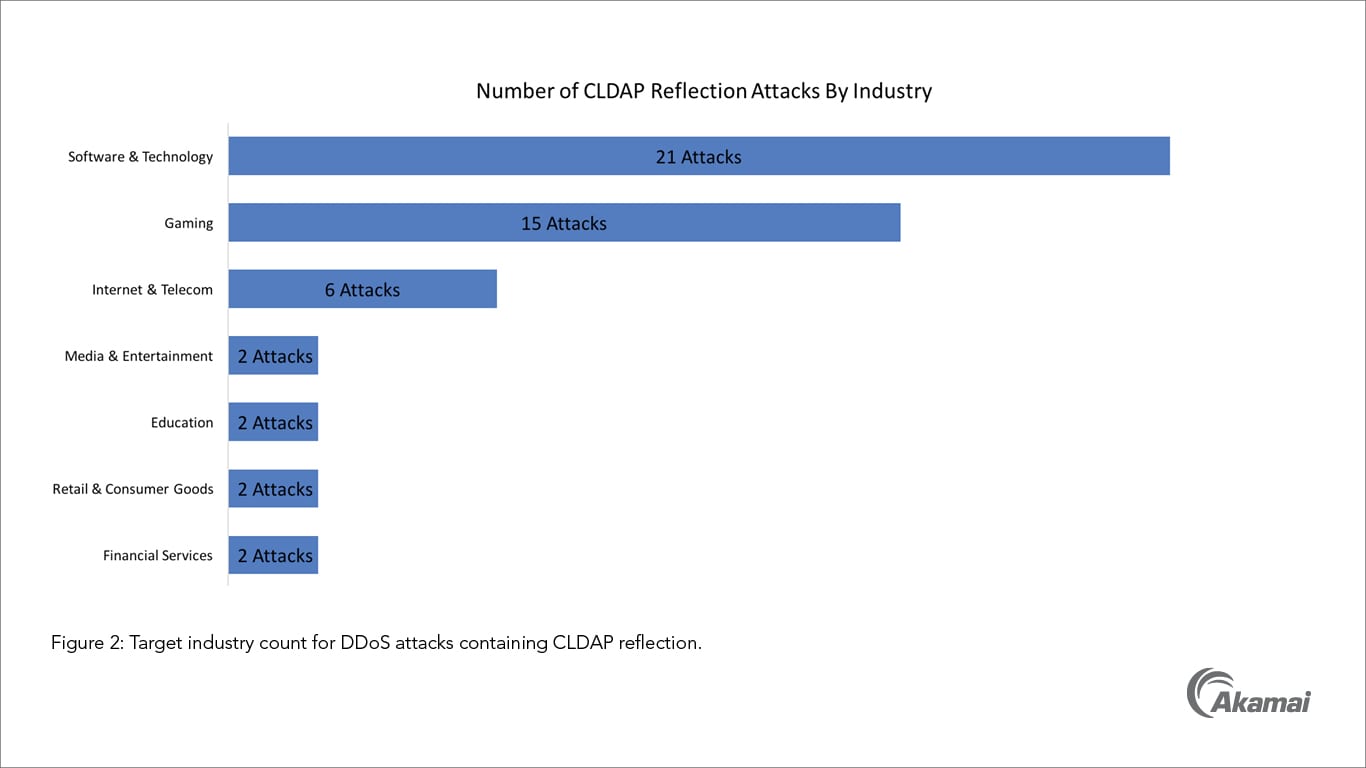
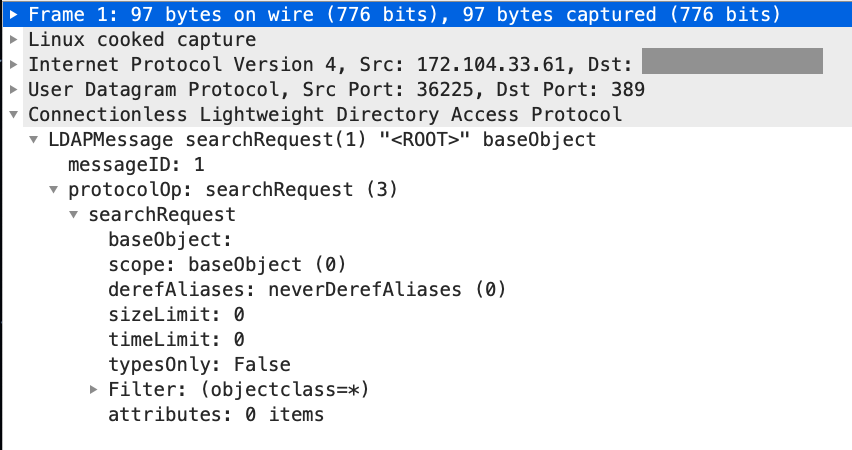
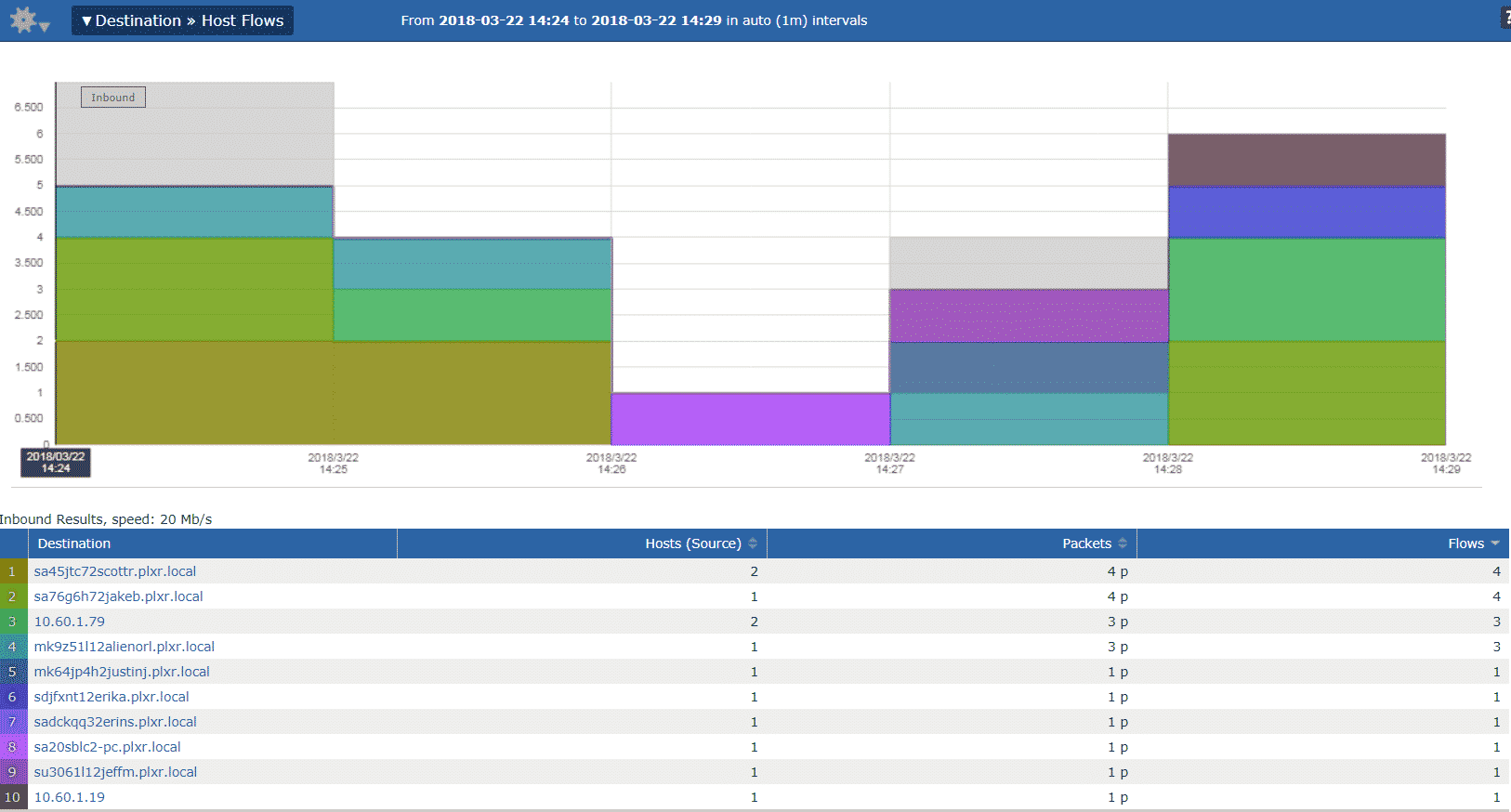
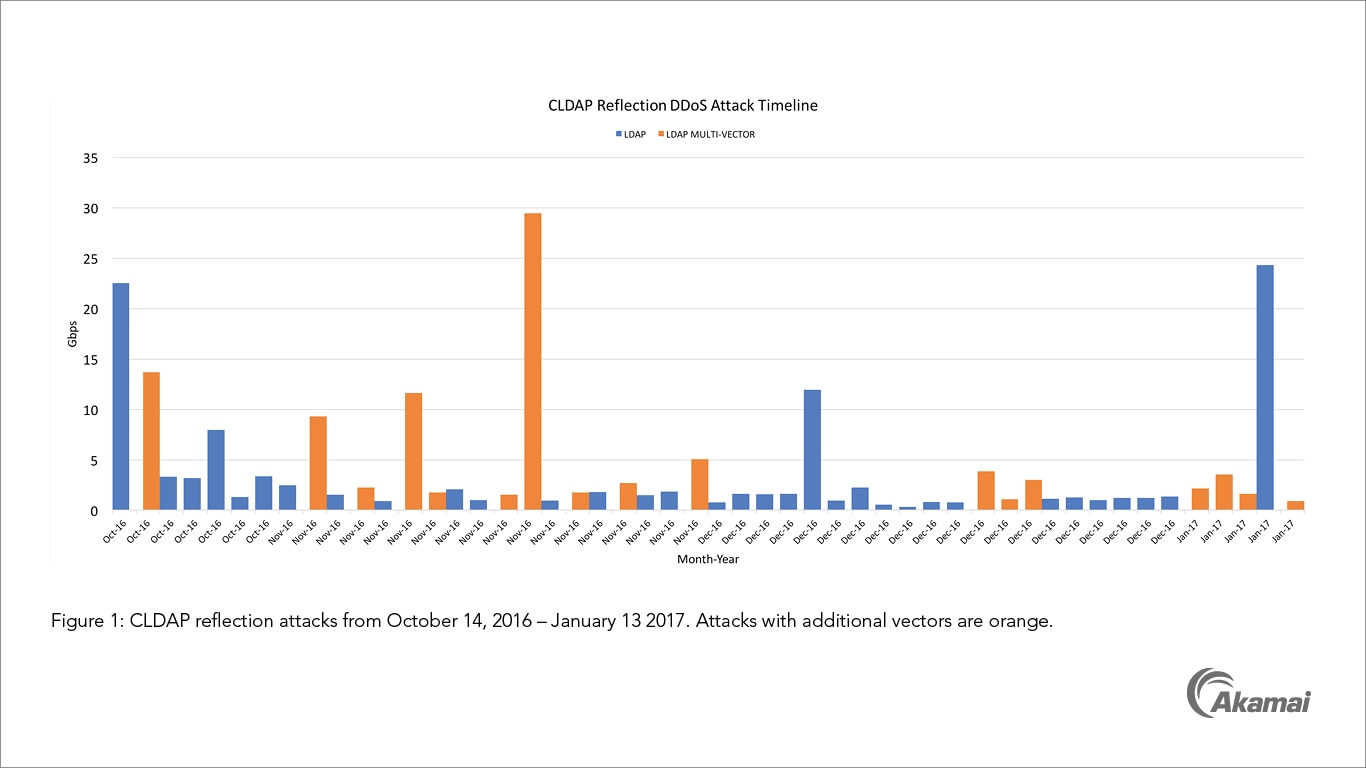
Possible CLDAP DDoS - But how is traffic coming from outside to inside with no open ports or NAT to ... - Cisco Community

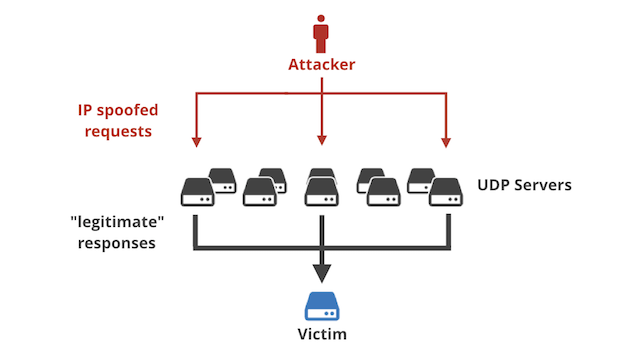
CLDAP Reflection Attacks back in style for the spring 2020 collection | DOSarrest Internet Security| DDoS Protection
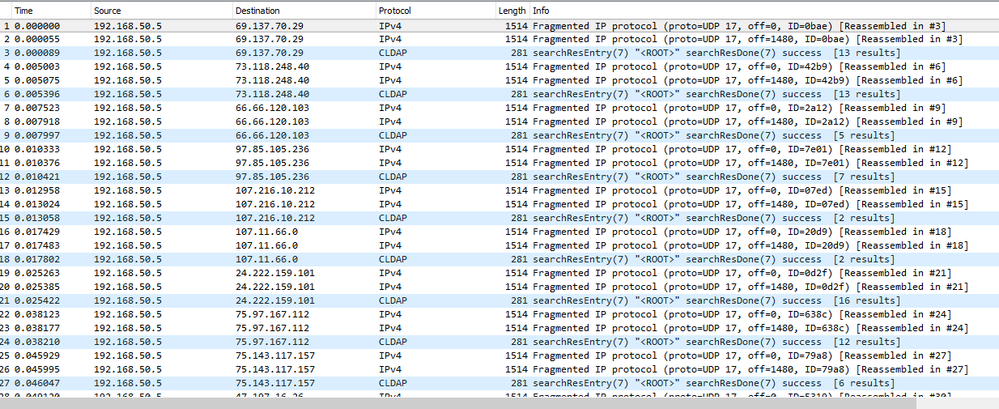
Possible CLDAP DDoS - But how is traffic coming from outside to inside with no open ports or NAT to ... - Cisco Community